
In the modern digital era, the evolution of technology has brought forth both remarkable advancements and at the same time unforeseen challenges. One such challenge is the intersection of cyber terrorism and gender-based violence, a pressing issue within the ever-evolving realm of cyberspace. Digital gender-based violence includes physical, sexual, psychological, social, political, or economic harm to women and girls because of their gender. The growing use of the internet and technological innovations has offered opportunities for communication, connectivity, and societal progress. However, this digital landscape has also become a safe space for malicious actors perpetuating gender-based violence through cyberterrorism. Exploring the complicated dimensions of cyber terrorism and gender-based violence, this research aims to shed light on the techniques, motivations, impact, challenges, and potential solutions surrounding this critical issue.
Cyberterrorism is the politically motivated use of social media, or even the internet as a whole entity to cause widespread panic, disruption, and often the spread of extremist ideologies. It is a new form of terrorism that is ever adapting to the new iteration of the resources on internet. There are several different methods to conduct online terrorist attacks; deploying malware, conducting Distributed Denial of Service (DDoS) attacks, hacking systems, manipulating information, and employing social engineering tactics. 1 All of these methods can be used to achieve the previously stated motivations, and are often used together simultaneously to be more efficient. The most commonly known method is referred to as a Distributed Denial of Service or a DDoS attack. The aim of a DDoS attack is to overwhelm the servers, devices, and network with false internet traffic created by the attackers. The attack makes the devices, server, and networks inaccessible to legitimate users, and creates a window of opportunity to steal data, corrupt files, or leave behind viruses. DDoS attacks are almost always successful due to the sheer quantity of connected devices to barrage a server or network with requests.2 Another commonly used method is hacking. While hacking is a broad and extensively complex method of attack, it can be used to achieve several different objectives including selling users data, extracting classified or proprietary information, spying, or disrupting information.
Understanding Cyber Terrorism and Gender-Based Violence
Although cyberterrorism is prevalent in many different forms, there is no official consensus on what constitutes cyberterrorism. This is important to understand as there are many different types of illegal activity online that could constitute as cyberterrorism. Since there is no definite answer to what cyberterrorism is and it is ever evolving, it is important to continuously study it to look for trends in the ways social media and the internet are used in acts of terrorism. The internet does not stop at domestic borders, which means it can be hard to apprehend and prosecute those who commit cybercrimes or cyberterrorism. Due to how quickly information is passed online, terrorists’ plans, ideologies, and radicalization can spread before officials are even aware of a terror group’s intentions. Any online terrorist group has the potential to attack private business, banking, and information networks which can have both domestic and global effects.
Evolution of Terrorism in the Digital Age
The evolution of terrorism in the digital age shows a significant shift in tactics, strategies, and impact due to technological advancements and the widespread nature of the internet. The rapid growth of the internet has brought about changes in the way terrorist organizations operate, communicate, recruit, and carry out attacks. The internet provides an expansive platform, enabling extremist ideologies to reach a vast audience and spread rapidly through social media, websites, and online forums. Terrorists are able to use the platforms to reach a wider audience and are able to spread panic, disruption, and extremist ideologies much more efficiently.
Global networking and recruitment of cyber terrorists involve leveraging the internet’s expansive reach to connect with individuals worldwide, propagate extremist ideologies, recruit sympathizers, and groom potential operatives for cyber attacks or other terrorist activities without ever having to meet in person. Online recruitment works so well because of the structure of many online forums. Online forums often offer a place where smaller groups of people interested in the same topic can meet and share a common interest. Terrorist groups are able to target specific groups of people online who can be easily manipulated with targeted propaganda. Extremist groups tailor their online messages or propaganda to target these specific demographics or vulnerable individuals, exploiting grievances, religious beliefs, or societal issues to attract recruits.
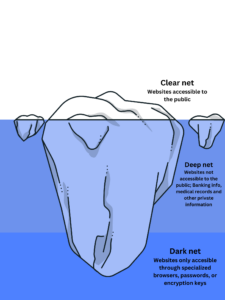
The digital age has significantly altered the landscape of terrorism, allowing groups to operate on a global scale, transcend physical borders, and reach a larger audience through newer technologies; the most used being the dark web. The dark web includes about 90% of websites on the internet while the clear net, what we use with Safari and Chrome, only include about 10%. 3 The dark web is a part of the internet that is encrypted from the public. Users must use a private browser, the majority of users use a browser called Tor, to access websites on the dark web. “When users access a site through Tor, their information is routed through thousands of relay points that cover the user’s tracks and make their browsing virtually impossible to trace.”4 This keeps most of the websites hosted on the deep web anonymous and private unless a user knows how to access the sites. The anonymity of the dark web has posed new challenges for law enforcement, governments, and technology companies in combating these threats while navigating the complexities of privacy, free speech, and security in the online sphere.
Gender Based Violence in Cyberspace
In the modern world, the widespread use of technology has not only revolutionized communication and connectivity but has also given rise to a new form of gender-based violence; within the cyberspace domain. This new method is full of various forms of digital aggression, poses profound challenges for women, can encompass cyberstalking, online harassment, distribution of revenge porn, and other malicious acts aimed at inducing fear, humiliation, or harm. The pervasive nature of these cyber-inflicted attacks extends beyond virtual boundaries, deeply impacting the lives, dignity, and safety of women in real-world settings. Yet, confronting these issues presents a complex issue of legal and societal challenges, where existing frameworks struggle to adequately address and protect against the multifaceted dimensions of cyber gender-based violence. This section aims to dismantle the forms of gender-based violence prevalent in the digital realm, analyze the detrimental impact of cyberstalking, harassment, revenge porn, and related activities on women, and explore the intricate legal and societal hurdles in effectively combating and mitigating cyber gender-based violence.
Digital Gender Based Violence
There are several different forms of gender-based violence in the digital realm. Digital gender violence can include sextorition, the use of a person’s sexual information for blackmail, to doxxing which includes sharing phone numbers, addresses, and other personal private information. 5 Other forms can include threats and hate speech. Another dimension of digital gender violence includes the rhetoric of those committing violence against women. Over 58% of women and girls have experienced some type of harassment or violence online. 6These individuals create online “sanctuaries” where they can freely express hateful speech and plans of violence against women.
Violence against girls and women online is almost always sexual in some manner. Perpetrators’ motives can range from revenge, anger, political agendas, sexual desires, to maintain societal status in their mind, or monetary gain. There are also groups of women that are more targeted than others including journalists, women active in politics, women with a public profile, women from minority or marginalized groups including race, gender, sexual orientation, or women with disabilities. 7
One of the most common forms of digital gender violence is the non-consensual creation or distribution of photographs, video, or audio for a sexual or intimate act. This method is multifaceted and often has several different ways of being carried out, but it is commonly referred to as “revenge porn”. Revenge porn however is a problematic term due to most perpetrators’ motivations extending far beyond revenge. For most, the term “revenge porn” also causes more harm than good to the victim, and typically focuses on the image and not the abuse. This method uses intimate photos, video or audio previously shared consensually or stolen through hacking in a non-consensual manner.These methods also includes secretly recording and distributing images of sexual abuse or consensual sexual activities, taking non consensual photos or videos in public to be shared online. Another type of gender-based violence includes the use of deepfakes which have become synonymous with online harassment and violence against women. Deepfakes are generated by software programs that use machine-based learning to swap one person’s face in a photo or video for another’s. The programs are being used to create fake pornographic material to distribute online. Most women who are targeted by deepfakes are women who hold positions of authority or celebrities, and it is used to try and discredit them. Attempting to discredit or damage reputation is a common motivation for attackers. In a UNESCO global survey, 41% of respondents reported being targeted by attacks that appeared to be related to disinformation campaigns specifically aimed at discrediting female journalists. Another type of violence includes cyberstalking, which involves persistent surveillance, threats, and intrusive behavior online, instills fear, anxiety, and a sense of constant vulnerability in victims. Online harassment, comprising abusive messages, derogatory comments, or hate speech, inflicts emotional distress, leading to psychological trauma, anxiety, and depression. Revenge porn, the non-consensual sharing of intimate images, causes immense humiliation, shame, and social ostracization for the victims, leading to severe emotional anguish and potential damage to personal and professional reputations. These forms of digital violence often extend beyond virtual spaces, impacting the physical safety, mental well-being, and overall quality of life for women.
The Impacts of Gender-Based Violence Online
The psychological toll, fear of escalation, and the perpetual invasion of privacy disrupts daily functioning and perpetuates a cycle of trauma that affects victims’ social interactions, mental health, and sense of security. The lasting effects of these online abuses emphasize the urgent need for effective measures to prevent and address digital gender-based violence, safeguarding the well-being and rights of women in the digital realm. Victims of online harassment or reputation damage due to online attacks are often forced to leave work, school, and communities to avoid humiliation. Victims can experience significant harm to their physical and mental health with symptoms including self-harm, depression, and potentially suicide. Post traumatic stress disorder is especially common in survivors. Young girls and women have reported problems at school, having lower self esteem or loss of confidence, mental or emotional stress, and feeling physically unsafe.8 The political impacts include women self-censoring themselves and restricting their personal daily use of the internet. Girls are also much less likely to enter into career fields of politics or journalism due to the violence and harassment women in these careers face. A UNESCO study of women journalists found that 11% of respondents missed work to recover from violence, 38% made themselves less visible, 4% quit their jobs and 2% abandoned journalism altogether. 9 Social media programs like X and Facebook attempt to regulate violence and harassment against women, but are regulated inconsistently. When not regulated the harassment and other violence simply become more pervasive. Due to the lack of consistent regulation on social media the perpetrators of the attack become more confident and are inadvertently invigorated to continue harassment.
Incel Culture and Its Role in Gender-Based Violence

The dark web is both a breeding ground and a sanctuary for individuals who hate women. The online communities that have been created encourage and support extreme attitudes of hatred, violence, and misogyny. These communities are part of the “Manosphere”, a larger body of online spaces that proliferate ideas of misogyny and opposing feminism. The members of these communities often refer to themselves as “incels” or involuntary celibates.10 Incels main ideologies revolve around the idea that they are unable to access sex due to women not being interested in them and “alpha males” stealing the women who may be attracted to them. They believe their lack of access to sex is completely due to outside forces and therefore placing blame on anything external to themselves. While violence against women is integral to the ideology of incels, there are three different levels of violence as the incel ideology is very broad and complex and the group can also encourage violence within members. One level is personal violence which includes suicidal thoughts and self harm on the part of the incel. Seeking out mental health support or self-help is highly discouraged by members. Members who attempt to get help or escape the community are often pulled back into the community by members convincing them that whatever woman they are interested in won’t be interested back. If any incels successfully leave the community, they are deemed “false incels” by the group.11 The second form of violence is interpersonal violence and has the basic theme of incel communities encouraging each other to hurt others. This can include “taking down” others if the incel is going to harm themselves. Intrapersonal violence from incels also include the harassment of women both online and in person. One method is known as “Chadfishing”; an incel will create a fake dating profile made to look like an “alpha male” or “Chad” only to string along women and then turn them down to crush their confidence. The final categorization of violence is societal. This is acts of violence targeted at societal groups, often mass shootings. The community generally idolizes violent attacks, gamifying the events for community pleasure (i.e keeping scoreboard rankings of perpetrators).12 The incel ideology revolves around a contradictory mix of disdain and longing for women. In essence, incels seek romantic relationships and sexual encounters with women; however, they also hold women responsible for denying them these opportunities. Incels believe they have a right to sexual encounters with women and when denied more than likely react violently in one or multiple ways.
The Dark Web, Encrypted Communication for Terrorist Activities and Gender Violence
On the opposite end of terrorists’ use of the internet is the dark web. While social media offers groups recruitment opportunities and the ability to share their message, the dark web offers an anonymous platform to share ideologies, hate speech, plans of attacks, and extremist narratives. The Dark web’s anonymity and encrypted channels provides a haven for the dissemination of extremist propaganda, recruitment, fundraising, and the exchange of tactical information, empowering terrorist entities with unprecedented capabilities to orchestrate cyber-enabled attacks. As monitoring and censorship of terrorist groups on social media becomes more prevalent, terrorist and extremist groups are moving more of their operations to the dark web. Initial contact with recruits is made on social media or the clear web, the publicly accessible side of the internet. Recruits are then usually given further instruction on how to access forums and chats on the dark web or encrypted messaging through apps like Telegram and websites such as 4-chan, 8-chan, and Reddit.13Terrorist or extremist groups also use the darkweb as an information storing system. Propaganda and other terrorist and extremist groups’ recruitment media is often removed from clear web sites and social media. Using the dark web and creating webpage or forums helps these groups both post and store propaganda media that will not be removed or censored. The Tor Network is the most commonly used browser to access the dark web. Tor program transmits information through the network of the computer by sending data through different networks that are operated by volunteer computers. Tor conceals the user’s identity and location and does not track the history of websites accessed any keep websites visited anonymous. Tor is well known for its freedom of speech policy. The browser encourages unrestricted access to the internet in societies or countries with strict internet censorship. The dark web can be used to help connect people, foster communication and share information with those whose internet and information accessibility is cut off. Notable websites like Facebook and The New York Times have launched versions of their websites on Tor to be more accessible to readers who were blocked from accessing the surface web page.14 While there are several different good and ethical uses for Tor and the darkweb, it is important to understand the darker, more disturbing side of the browser.
Challenges and Responses to Gender Violence Online

When trying to mitigate the pervasive issues surrounding gender-based online violence one of the key challenges is the lack of definition for cyberterrorism or gender-based violence online. There is not one way that perpetrators commit attacks so having a definition that is able to cover all types of attacks and violence is nearly impossible. Another issue is the constantly changing environment of cyberterrorism. As we progress further into the digital age, cyberterrorists will continue to change their tactics online, adapting to avoid being detected by law enforcement. There is no one specific “right” way to combat these issues legally due to the methods cyberterrorists use to cover their tracks and remain anonymous using the dark web to communicate, plan, and recruit. In response to these challenges, a variety of mitigation strategies, legal reforms, technological innovations, awareness campaigns, and support services, all seek to create safer and more inclusive online environments. This exploration delves into the nuanced challenges faced in combating gender violence online and endeavors to illuminate the multifaceted responses and mitigation efforts required to foster a digital space free from gender-based abuses.
Legal Frameworks and Enforcement Challenges
Many jurisdictions lack specific laws tailored to address the subtle distinctions within the different types of cyber gender-based violence. Existing legislation might not comprehensively cover various forms of online abuse, leaving gaps in legal protection. Even where laws exist and are in place, challenges in enforcement persist due to the global and often anonymous nature of online spaces. Jurisdictional complexities and the transnational aspect of the internet hinder effective law enforcement and prosecution. COVID-19 saw a massive uptick in the amount of violence against women and girls digitally. One possible solution may lie in tech companies more so than legislation. Lobbying tech companies to develop programs that allow individuals to control their online algorithms to block topics, control privacy, or customize their interaction to protect themselves against abusive behaviors. Sharing non-consensual pornography includes images taken or sent consensually during a relationship, hidden recording or photos, photos or video stolen from electronic devices. There is not specific federal law against revenge porn but several states have their own civil and criminal charges for sharing non-consensual pornography. However, there is a federal civil cause of action for victims. This means a complainant can seek compensatory and punitive damages against someone who non-consensually shares private pornography. Two states currently do not have any laws banning sharing non-consensual pornography; Massachusetts and South Carolina.
The Biden-Harris Administration recently announced an expansion of the technological abuse section in the reauthorized Violence Against Women Act. The DOJ (Department of Justice) will implement provisions in the Violence Against Women Act that will include “technological abuse”. This will recognize the importance of addressing technological abuse as it intersects with domestic violence. The office of the Attorney General is creating a national standard to prevent and address different cybercrimes like cyberstalking or non-consensual distribution of pornography. They will also be directing the FBNI to improve data collection regarding cyber crimes. The White House will also be providing more resources to access services for survivors of cybercrimes and security to prevent more crimes. 15
The relationship between terrorists’ usage of the clear web and the dark web emphasizes the ever changing world of online extremism. While social media enables recruitment and message dissemination, the dark web offers an anonymous haven for the propagation of extremist ideologies and planning of cyber attacks. Perpetrators moving toward the dark web is becoming more popular as monitoring and censorship on social media platforms intensify. Simultaneously, combating gender-based violence online presents enormous struggle, notably the lack of a specific definition for cyberterrorism or online gender-based violence. The evolving tactics of cyberterrorists further complicate legal interventions. As the digital age evolves, the need for collaborative efforts to foster inclusive and safe online environments becomes increasingly important, highlighting the necessary nature of ongoing solutions to counter gender-based abuses. While legislative gaps persist, including 3 states not having any laws protecting individuals against cyber harassment, promising initiatives emerge, notably through the Biden-Harris Administration’s expansion of the Violence Against Women Act. This reauthorization acknowledges the significance of combating technological abuse by integrating provisions to address cyber crimes intersecting with domestic violence. Emphasizing technological advancements and collaborative efforts with tech companies holds promise in empowering individuals to control their online interactions and privacy, potentially stopping abusive behaviors.
- Cloudflare. (2023). What is a DDoS Attack? https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/. ↵
- Cloudflare. (2023). What is a DDoS Attack? https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/. ↵
- https://usa.kaspersky.com/resource-center/threats/deep-web ↵
- https://sopa.tulane.edu/blog/everything-you-should-know-about-dark-web ↵
- UNPF. (2023). Technology-Facilitated Gender-Based Violence: A Growing Threat. https://www.unfpa.org/TFGBV ↵
- UNPF. (2023). Technology-Facilitated Gender-Based Violence: A Growing Threat. https://www.unfpa.org/TFGBV ↵
- Association for Progressive Communications (APC). From impunity to justice. Exploring corporate and legal remedies for technology-related violence against women 2012- 2015. https://genderit.org/onlinevaw/ ↵
- Plan International, ‘Free to Be Online?’, 2020, p. 28. ↵
- UN Women. (2021). ACCELERATING Accelerating Efforts to Tackle Online and Technology Violence Against Women and Girls. Retrieved from https://www.unwomen.org/sites/default/files/2022-10/Accelerating-efforts-to-tackle-online-and-technology-facilitated-violence-against-women-and-girls-en_0.pdf ↵
- Voogd, A., & Scheele, R. (2021, June). The Incel Phenomenon: Exploring Internal and External Issues Around Involuntary Celibates. Retrieved from https://home-affairs.ec.europa.eu/system/files/2021-08/ran_cn_incel_phenomenon_20210803_en.pdf ↵
- Voogd, A., & Scheele, R. (2021, June). The Incel Phenomenon: Exploring Internal and External Issues Around Involuntary Celibates. ↵
- Voogd, A., & Scheele, R. (2021, June). The Incel Phenomenon: Exploring Internal and External Issues Around Involuntary Celibates. https://home affairs.ec.europa.eu/system/files/2021-08/ran_cn_incel_phenomenon_20210803_en.pdf ↵
- Malik, N. (2018). Terror in the Dark. The Henry Jackson Society, 1(1). https://henryjacksonsociety.org/wp-content/uploads/2018/04/Terror-in-the-Dark.pdf ↵
- Malik, N. (2018). Terror in the Dark. The Henry Jackson Society, 1(1). https://henryjacksonsociety.org/wp-content/uploads/2018/04/Terror-in-the-Dark.pdf ↵
- House, T. W. (2022, May 4). Fact Sheet: Presidential Memorandum Establishing the White House Task Force to Address Online Harassment and Abuse | The White House. vhttps://www.whitehouse.gov/briefing-room/statements-releases/2022/06/16/fact-sheet-presidential-memorandum-establishing-the-white-house-task-force-to-address-online-harassment-and-abuse/ ↵




12 comments
Natalia De La Garza
This is an outstanding exploration of the intersection of cyber terrorism and digital gender-based violence, offering a clear, well-organized, and nuanced understanding of a critical issue in the digital age.
Kaitlyn Villanueva
What a great article!! We see lots of gender-based struggles in our everyday life but highlighting how this can occur through technology is very powerful. The internet is a place that people are constantly spending their time on; its concerning to see how negative this place can be and what impacts it has on gender. This research was amazing, awesome job!
Jordan Robbins
Hi, this is so cool! I like how you acknowledged the gender-based struggles even through the phone. You explained everything so well and made it very thorough to a “T”. I do wonder if you’ve experienced any sorts of struggles you stated in the explanation of everything. But, yes everything was said so well and I learned a lot about different forms of social issues in todays age
Silvia Benavides
This was a very eye-opening article the internet is such an amazing place to learn but it must also be acknowledged that the internet holds a powerful impact on various aspects of society. I loved the intersections of cyberterrorism being presented.
Carlos Anthony Alonzo
Your research sheds light on the complex relationship between social media and affects toward women’s well-being. The longitudinal approach provides valuable insights into how usage patterns evolve over time and their impact on psychological health. Yet, considering the multifaceted nature of social media, future studies could delve deeper into specific platform dynamics and user interactions. Great article!
Fernando Milian
It’s scary to think about how the internet, which has so many positives, can also be a place where women are attacked just because of their gender. The part about different methods like DDoS attacks and hacking being used for gender-based violence is quite shocking. I’m glad to see there are some efforts to fight back, like the changes in the Violence Against Women Act, but it seems like there’s still a lot to be done. It makes me think about how important it is for us to be careful online and support each other to make the internet a safer space for everyone, especially women and girls who are targeted.
Stela Naomi Sifuentes
Addressing the root causes of gender-based violence requires challenging gender stereotypes and promoting equality in all aspects of society. This includes advocating for equal rights and opportunities for people of all genders in education, employment, and political representation. Well said Lily!
Sebastian Hernandez-Soihit
Well put togheter article and a soberting reminder of the power of technology, one which often goes unnoticed by everyday users that indulge in it a little too much. Amazing job!
Nicholas Pigott
Hi Lily! Your article is exemplary at showcasing one of the biggest rising dangers to women as we form our era into the digital age each passing day. With new eras comes new threats, threats that particularly harm specific people and demographics disproportionately. Your article is powerful and informative, and raises awareness to the issue at hand. Congratulations on your nomination!
Jonathan Flores
Your article has depth on a level that is unmatched by many other articles, which is greatly commendable. In addition, you covered a topic of great importance in our ever-increasingly technology dependent society. It goes without saying that abuse of technology has great consequences and I think you did a great job at explaining them. Overall, the piece is well written and covers an interesting topic, so well done.