Technology has become a fundamental part of our daily life. Nowadays, every modern process uses computers to perform their actions. Until the late 1980s, all college assignments were done either by hand, or by typewriter. Today, in the twenty-first century, everything is done on computers. In the last century, letters and telegrams were used to communicate written material over long distances. However, today just one click is enough to send a message to the other side of the world. Technology is ubiquitous; now all banks and online stores place absolute trust in the internet to make bank transfers of often astonishingly large monetary sums. However, it is not all a bed of roses for the internet. Just as every thesis has its antithesis, the internet world found its executioner in computer viruses. There are many unfortunate people who, because of computer viruses, end up losing everything, from their images and music, to valuable works, and even thesis projects. We all know about the existence of viruses, but very few of us really understand how they work, how they propagate through the web, and the magnitude of the effects of viruses on our devices and our lives.

Hated by all, the computer virus is the number one enemy of all who own a laptop, a computer, tablet, and even a smartphone. Its construction is simple but can be devastating. The virus is a piece of software based on various characteristics and with innumerable “themes.” In the same way as a biological virus, it attacks the host (in this case, the computer) and begins to infect many others to increase its reach. Basically, the virus is hidden in a program or document and is released when these files are executed. This plague of the electronic age emerged in the 1970s, initially only for programmers to demonstrate their skills. However, it ended up becoming a very lucrative criminal activity. Today, there are malware (malicious software) being spread by email or infected sites, and even by artificial intelligence, which simulates real conversations in chats to convince the victim to click on a contaminated link.1
The malicious software can be of various types, of which two are the most common in the world of computer science. Perhaps the best known type of malware is the Trojan Horse, which is as treacherous as its namesake in Greek mythology. A Trojan typically disguises itself as a normal and benevolent application during its installation. The users who receive the Trojans are convinced to install them and execute them because they have received them from a trusted source. Once executed, a Trojan can cause severe damage, such as capture of bank passwords, credit card data, social network passwords, etc. Another common group of malware are worms, a particularly harmful subclass of viruses that are distinguished by their ability to spread without human action, using all communication capabilities available in a device to self-distribute.2 Worms replicate themselves inside an infected device, creating thousands of copies of itself, in order to spread more quickly and prevent an antivirus from removing them before causing damage and contaminating other devices. Worms are also used to open ports on the infected user’s device, allowing a hacker total remote control of all available resources on the infected device.3
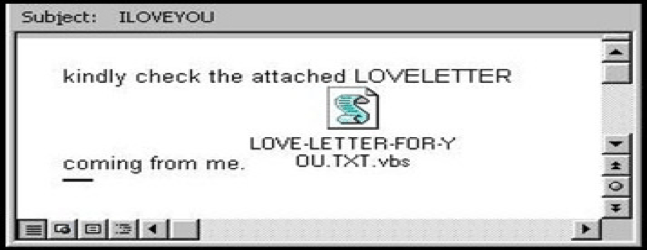
A colossal number of viruses churn through the internet, but among all the stories that can be told about viruses, there is one that stands out among all the others: the virus “I Love You,” the one that took advantage of the innocence of a secret message of love that destroyed 45 million computers! The story behind the catastrophic message created by Onel de Guzman, will surprise many people, including you. Without further ado, the story of one of the most lethal thesis projects in history: I Love You.4

On May 4, 2000 computer networks around the world were invaded by the virus that has until today earned the title of fastest propagation invader. In a matter of hours, the “Love Bug,” as the virus became known, infected more than three million machines. It came with a message in which both the subject “I Love You” and the attachment “Love-Letter-For-You” appealed to the curiosity of the recipient. To further disarm the victim’s defenses, the e-mail came almost always in the name of a friend or acquaintance.6 Although it had no destructive load, the love letter caused deep havoc by producing an unprecedented e-mail branch that congested servers around the world, causing billions of dollars of losses for companies around the world. According to the consulting company Computer Economics, the losses were around twelve million dollars.7 Not even the “Code Red” and “Sircam” viruses, which in 2001 caused an injury of 3 million and 1.5 million dollars, respectively, overcame this virus that certainly entered into history as the most devastating of the global network of computers.8
“The teachers did not like my work, they rejected my thesis. They said it was against the policy of the faculty and everything just because I used the word steal instead of access. It was a simple matter of vocabulary,” recalls the “Clyde Barrow” of computer hacking and author of one of the greatest computer disasters in history.9

The truth is that his idea was brilliant, as well as perverse. If the virus “I love you” spread so quickly, it was because everyone liked the idea of receiving an anonymous love letter. The famous love letter was the product of the disgust of a disgruntled student with his faculty, the revenge of Onel, because they rejected his thesis. Clerks, stockbrokers, politicians, firemen, or journalists, people here and there, opened the message of the supposed admirer or secret lover who began his letter proclaiming his love. Just by clicking it, the program created by Onel de Guzman began to work, that is, to eliminate. First, the virus infected the computer itself and destroyed the information on the hard disk. Then the virus forwarded the electronic message to all the addresses that the receiver had stored, in an unstoppable chain. Within twenty-four hours three million computers had been infected and within a week there were already more than 45 million computers unusable.10 Probably the final number of victims of what some experts still qualify as the most virulent, devastating, and costly virus in history, will never be known. The teachers of the AMA School of Computer Science could not believe it when, three months after receiving the thesis of their model student, they realized that the virus that was going around the world worked exactly as Onel had explained in his dissertation. His thesis, which he called “The Trojan Horse,” still circulates on the Internet today and is the bible for many computer hackers, teachers, students, and curious people.11
What happened to the author of one of the most serious cyber catastrophes in history? Absolutely nothing. The Government of the Philippines had with Onel case its first cybercrime in its history. The Philippine authorities found a total absence of cybercrime legislation with which to prosecute the alleged perpetrator. After the appearance of the virus “I love you,” the government of the Philippines created a law on computer crimes, but it could not be applied retroactively and therefore did not affect the author of the love letter.[12: Robert Frank, “Lacking Laws, The Philippines Throws Out ‘Love Bug’ Case,” Wall Street Journal – Eastern Edition, (August 22, 2000): 20.]

Onel de Guzman just needed one computer and an internet connection to be able to invade more than 45 million computers in just one week.12 De Guzman’ virus was so powerful that it was even able to penetrate one of the most powerful cybernetic systems in the world, the Pentagon of the United States of America. Yes, it is no joke, a college student was able to infect four classified military systems of one of the safest and most sheltered facilities on the planet.13 If the Philippine was able to crash one of the most powerful systems in the world, monitor financial accounts, steal personal information and messages, we must be ever vigilant before we casually click on any email attachment.14 A computer virus, like a biological one, does not distinguish social condition, economic power, political position, or any other difference. They are there, waiting for a click, which will allow them to do what they do best: destroy everything in their way. Let’s be always alert.
- Funk & Wagnalls New World Encyclopedia, August 2016, s.v. “Computer Virus.” ↵
- Roberta D. Anderson, “Viruses, Trojans, and Spyware, Oh My; The Yellow Brick Road to Coverage in the Land of Internet Oz ,” Tort Trial & Insurance Practice Law Journal no. 2 (June 2013): 529. ↵
- Salem Press Encyclopedia Of Science, January 2017, s.v.”Computer viruses and worms,” by Linda Volonino. ↵
- “I Love You’ virus,” Journal of Property Management 70, no. 2 (March 2005): 9. ↵
- Adam Cohen, “School for Hackers,” Time Magazine 155, no. 21 (May 2000): 59. ↵
- Mark Ward, “A decade on from the I Love You bug,” BBC News (May 2010), 5. ↵
- Bob Edwards, “Analysis: Projected cost of damages caused by the ‘Love Bug’ computer virus,” Morning Edition (May 2000): 23-24. ↵
- Keith A. Rhodes, Information Security: Code Red, Code Red II, and SirCam Attacks Highlight Need for Proactive Measures (Washington D.C.: U.S. General Accounting Office, 2001), 23-24. ↵
- Rajiv Chandrasekaran, “Student Proposed Virus in Thesis; ‘Love Bug’ Probe Focuses on Filipino College Senior,” The Washington Post, (May 2000): 7-8. ↵
- Frank Prince, “Love Bug’ Redux: Keeping Alert to Danger,” Community Banker Journal, (June 2000): 45. ↵
- Rajiv Chandrasekaran, “Student Proposed Virus in Thesis; ‘Love Bug’ Probe Focuses on Filipino College Senior,” The Washington Post, (May 2000): 7-8. ↵
- Bob Edwards, “Analysis: Projected cost of damages caused by the ‘Love Bug’ computer virus,” Morning Edition (May 2000): 23-24. ↵
- Mark Lander, “A Filipino Linked to ‘Love Bug’ Talks About His License to Hack,” The New York Times, (October 21, 2000): 1. ↵
- Karen D. Loch,”Threats to Information Systems: Today’s Reality, Yesterday’s Understanding,” MIS Quarterly 16, no. 2 (June 1992): 177. ↵


80 comments
James Clark
The entire article seems ridiculous especially considering the importance that we place on cyber security now. However, we are still learning and in the baby years of technology. It’s crazy to see how far we have progressed in technology in the short amount of time that computing has been around. The idea of a Trojan horse virus is extremely smart and forward thinking considering how early programming was and the power behind the languages at the time.
Sideshow Bob
I was employed at a large State Gov’t agency in the US at this time.
Ironically enough, in preparation for Y2K, we had all been upgraded from 386/486 processors with DOS operating systems (blue screen with “backslash” commands) with Word Perfect & Lotus 1-2-3, to brand new Pentium’s with Windows OS, Windows email, Word, Excel, Calendar, etc. So, in May 2000, for most non-tech Gov’t employees, email communication was a fairly new phenomenon. Even owning a home computer was not “everyday” yet, as they were still $1,000, & an “ISP” was $30/month plus long distance phone charges for 56k dial up service.
Now I was an Engineer (albeit “brick & mortar” – ie Civil) & had owned a home PC for years, so was pretty familiar with using email & the threat of viruses. But most of the folks at my agency weren’t, being administrative, accounting, legal, etc.
So when this virus first struck, our Inboxes were overwhelmed with “ILOVEYOU” messages from folks at our agency, some of whom we knew. “Helpdesk” sent a message pleading with us to NOT click on the file! But many didn’t see it as it was buried amongst all the ILOVEYOU spam, so folks kept opening it & sending even more messages. IT Finally had to shut down all email & asked Management to hold staff meetings informing employees NOT to click on the virus. They even provided a “slideshow” in (brand new at the time) PowerPoint.
This would have been sufficient, or you’d have thunk, lol. IT “scrubbed” all the servers, reset all email, sent out multiple messages telling everyone NOT to click on the file. But, lo & behold, OF COURSE folks kept clicking away, re-infecting everyone all over again. IT went thru several iterations of this. In my Engineering unit we would sit & laugh at the names of the fellow employees who were Guilty of opening the file, even after weeks of this nonsense. They were all inevitable co-workers we considered to be total Twits in doing their jobs. We would exchange Stories about co workers that one of us knew but the others didn’t, citing examples of them doing their jobs Poorly / Fubaring things badly. It became a vast Social Experiment of sorts. “Let’s See How Stupid Some People Are” – “Oh They’re VERY Stupid, Indeed!”
Jacqueline King-Mackinnon
This is why many people have a fear of computers , they can destroy lives by making one silly mistake by opening a dodgy email.
Emilia Caballero Carmona
Hey Josemaria, your article was so interesting to read! I do not know anything about computer viruses and how they work, but we live in a technology filled world and it is important to learn this. Your article was great because for a person like me who doesn’t know much about this topic, you provided really good and detailed information and kept it simple and understandable which made sense to me.
Elizabeth Santos
The pettiness of this frustrated student made for such an interesting occurrence and this fascinating article. It was such a smart move to have this anonymous love letter be sent from people the victims knew. Reading this article was another reminder of how scary technology can be, and how even more frightening its users can be. It’s also bizarre that even top security sites were affected by the virus.
Cristianna Tovar
Before reading this article, I had no idea that viruses were first used for programmers to demonstrate their skills. I also wasn’t aware of the different types of viruses and their names, such as Trojan and worms. I thought it was interesting that the “I Love You” virus had included the names of the victims’ friends because it made it easier for people to believe that they were actually receiving a love letter. I was shocked to learn that a simple click of the wrong link could cause such havoc and ruin the privacy of millions of people – in this case – 45 million people, including the systems at the Pentagon!
Alin Bocardo Felix
It is amazing how far Onel went to prove his thesis, and in a way, humorous. He created this terrible virus as a hypothetical originally but was driven to release it to the world. Although it was a ‘success’ in the sense that it worked just the way he planned, it was a tragedy for 45 million computers. The name given to the virus by Onel, The Trojan Horse, also contains a bit of humor, in the fact that it disguised itself and then released a multitude of issues at once.
Vanessa Quetzeri
Viruses are really scary; I remember always being told not to click on pop-ups as a kid. It is crazy how one person could invade 45 million computers, some of these including the world’s most guarded computer systems. The message ‘I love you’ is clever because it doesn’t seem all that threatening, which increased it’s an appeal to the average internet surfer.
Patricia Arechiga
This article was a reminder of how much time I spend on the internet and with that includes providing personal information via online shopping and such. I think it is crazy how much information we provide without truly noticing nor reminding ourselves of the dangers that come with it. I remember being young and seeing pop ups and quickly exiting out of the page due to fear. I think it is pretty incredible how Guzman was able to hack into some of the most protected cybernetic systems in the world. However, at the same time, it is nerve-racking to see the power one mind can sustain.
Cynthia Perez
Of course everyone hates viruses because of how detonating they are to our everyday technological devices or equipment. Also not to praise Onel de Guzman or whatever but what he created is truly astounding, something that could spread a simple message for people who were gullible enough to open it. It’s a fairly small and yet largely manipulative tactic used by a single person and it’s pretty ironic considering the message being “i love you”. Admittedly I myself would probably be fond of that message because of its randomness and quality of being curiosity inducing, which makes many people out there alike, targets and vulnerable to these attacks. It will remain a growing problem with unattainable solutions the further advanced technology gets.