April 19, 2023
The Use of Biometric Systems and Data Beyond Agreed Consent
Electronic devices including phones and laptops, have various accessibility measures allowing a user to lock a device and restrict access to other individuals. Many of these security measures include biometric identifiers that use the individuals’ physical features. The more common identifiers include fingerprints or facial recognition, but some other methods include eye scanners, voiceprints, and scanning’s of the hands or face. 1 Biometric data can also be accessed through other smart devices like smart watches and fitness trackers that are often worn by those looking to maintain or track various health analytics. 2 While the uses of biometric identifiers has became more mundane and integrated into everyday life, there should be more caution should be taken in regard to how data is stored and used. If biometric data is to be used to be stored for longer than a year, and used for reasons outside of its initial purpose, it should be required for individuals to remain informed on its status and provide consent for its collection and use. Any data collected should be used without the consent of the individual as this would be a major ethical concern that imposes on the privacy of individuals. Although the identifiers and data may not be used around the clock by consumers, some questions that might pop up are “what happens to my data when I’m not using it?”, “where does it go?”, “can anyone else see my information”? Here is where there ethical concerns arise in the use of biometric data beyond an individuals consent.
A February 2022 report analyzed how different states currently use or intend to implement the Biometric Information Privacy Act (BIPA) when it comes to how biometric data is handled. BIPA was originally enacted in Illinois of 2008 as a way to monitor and regulate the use of biometric data amongst various businesses and other avenues. 6 According to the report there are only 9 states with existing laws for biometrics and 22 states with proposed laws. For the states that have existing biometric laws, there are similarities between the retrieval, destruction and disclosure concerning the data, though there are some differences. For example, in Texas an individual whos traits are being recorded must be informed of what is being done and subsequently must consent to the process. Further, the data is to be destroyed within the first year of its extraction and if those that have the data were to sell or distribute it without the individuals consent, they would receive a civic penalty. Whereas in Oregon, facial recognition is not allowed to be collected in public areas that surround Portland. 7 These differences in legislation and how few states have any laws put into place, show that there is a lack in biometric law standards on both the state and federal level. As a result, attacks on biometric systems and data put individuals at a high risk of having information stolen, used, or distributed without consent.
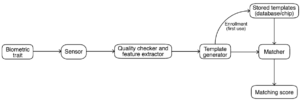
There are several ways in which a biometric system could be attacked, this may include hacking, a direct attack on the system and/ or an indirect attack to the system. In a direct attack, the sensor of the system is affected in that rather than using the real biometric trait, a fake or replicate is used and placed in front of or on the systems sensor. The fake or replicate trait can be anything from a silicon finger(print) to holding up a photo in front of a face scanner. In either case, the sensor then goes through the process of trying to match the unauthentic trait with the ones that have been collected and stored in the system. This is in contrast to an indirect attack that manipulates the inside of the system rather than the sensor. By doing this, false positives are returned to the system and access is granted. 8 With any of these situations, if the system is breached, then the likelihood of an individuals biometric data and personal information being stolen and used for purposes outside their agreed purpose is increased. Such a situation can be seen in the court case of the State of Texas vs Meta Platforms, more specifically Facebook.
In the court case, Facebook was accused to taking biometric information from uploaded pictures and videos that were put up by its members to be shared with the people they knew- not to be used for any other purpose. The biometric data that was being retrieved from the photos and videos through a service they implemented known as tagging. Tagging would let the user identify individuals in the photo to let others know who they were, but once this act was done the information was then analyzed through Facebook and used as part of an algorithm for further individual identification.

This information became a part of the system’s facial recognition technology that would map out users and non-users facial geometry for better identification and tag suggestions. It is stated that Facebook did not receive or obtain consent from its users, let alone non-users consent to keep track of and record their facial makeups. Moreover, it is also mentioned that “Facebook intentionally avoided using the term “biometric” to describe Tag Suggestions, because it knew that doing so would “scare people off.” Facebook also was distributing members personal information to outside/ third party sources that then further distributed the data. Further infringement was done to those who were not a part of the community but that were seen in the photos and videos that were being uploaded to the site. Biometric data was failed to be destroyed within the one year since its procurement and as such was also a violation to individuals. The State of Texas has asked that Facebook make amends by no longer obtaining biometric data illegally, destructing the data that is past its destruction date and been collected under false pretense, do away with the system that collects such information, and get back any of the data that had been disrupted to outside sources. 9
Although the storage and use of biometric data/ systems can be subjected to data breaches and non-consented use as seen with the State of Texas vs Meta Platforms case, there are some positives to its applications and use. One example is how use of biometric systems add for an extra layer of security for everyday technology. Use of fingerprints and face features has become a common application for cell phones and laptops to remain locked until the individual, whose features have been added to device, is able to unlock it. By using biometrics, only those that have been added to the devices biometric list/ log are able to open it. In some cases, it may be hard for even the user to get access into their own device if something is obstructing the sensor/ camera. For example, if the finger used to get access into the device is wet, the phone or laptop will more than likely not open as a result of the water obstructing the fingerprint. This comes to show the level of security that the use of biometrics offers. Along with its more mundane uses, biometric systems and data can also be used in law enforcement and with forensic science.

Biometrics have been able to be used as a tool for law enforcement and as forensic evidence through the use of fingerprints, face imaging, DNA, palm prints, the iris, and voice data. 10,11 The use of palmprints for example can help in a forensic science scenario because similar to fingerprints, the palm contains patterns and minutia that are unique to everyone and when analyzed or compared to ones from known individuals, a match can be made from the unique traits. The palm prints may also be subjected to a palm print identification system where an image of the print is created and key features are recorded to match the obtained print. An example of a database that can be used to compare and identify prints is the Integrated Automated Fingerprint Identification System (IAFIS). This database is maintained and monitored by the FBI and is used to to compare obtained prints against “70 million subjects in the criminal master file, 31 million civil prints and fingerprints from 73,000 known and suspected terrorists process by the U.S. or by international law enforcement agencies.” 11 As a result of the large number of prints IAFIS database and other biometric databases as well, there should be higher restrictions and standards put into place for federal and state agencies to be able to have access and use biometric data as it can further be used to aid in their investigations.
As seen previously, the use of biometric systems and data are ones that should not be taken lightly. Such systems are being more incorporated into daily lives and activities and therefore require higher standards and laws to ensure the safety and privacy of the data. The addition of such laws would also allow for companies like Facebook, as well as other individuals to be held accountable for the use of biometric data beyond a user’s consent.
- Nguyen, Fiona Q. n.d. “The Standard for Biometric Data Protection.” CYBER WARFARE 7. ↵
- Arnold, Jason F., and Robert M. Sade. 2017. “Wearable Technologies in Collegiate Sports: The Ethics of Collecting Biometric Data From Student-Athletes.” The American Journal of Bioethics 17 (1): 67–70. https://doi.org/10.1080/15265161.2016.1251648. ↵
- Rebera, Andrew P., Matteo E. Bonfanti, and Silvia Venier. 2014. “Societal and Ethical Implications of Anti-Spoofing Technologies in Biometrics.” Science and Engineering Ethics 20 (1): 155–69. https://doi.org/10.1007/s11948-013-9440-9. ↵
- Rebera, Andrew P., Matteo E. Bonfanti, and Silvia Venier. 2014. “Societal and Ethical Implications of Anti-Spoofing Technologies in Biometrics.” Science and Engineering Ethics 20 (1): 155–69. https://doi.org/10.1007/s11948-013-9440-9. ↵
- Pocovnicu, Adrian. n.d. “Biometric Security for Cell Phones” 13 (1). ↵
- McMahon, Michael. n.d. “Illinois Biometric Information Privacy Act Litigation in Federal Courts: Evaluating the Standing Doctrine in Privacy Contexts.” SAINT LOUIS UNIVERSITY LAW JOURNAL 65. ↵
- “U.S. Biometric Laws & Pending Legislation Tracker.” Bryan Cave Leighton Paisner – U.S. Biometric Laws & Pending Legislation Tracker. Accessed March 11, 2023. https://www.bclplaw.com/en-US/events-insights-news/us-biometric-laws-and-pending-legislation-tracker.html. ↵
- Rebera, Andrew P., Matteo E. Bonfanti, and Silvia Venier. 2014. “Societal and Ethical Implications of Anti-Spoofing Technologies in Biometrics.” Science and Engineering Ethics 20 (1): 155–69. https://doi.org/10.1007/s11948-013-9440-9. ↵
- State of Texas v. Meta Platforms Inc., Ken Paxton Attorney General of Texas (District February 14, 2022). Retrieved March 11, 2023, from https://www.texasattorneygeneral.gov/news/releases/paxton-sues-facebook-using-unauthorized-biometric-data. ↵
- Jain, Anil K., and Arun Ross. “Bridging the Gap: From Biometrics to Forensics.” Philosophical Transactions of the Royal Society B: Biological Sciences 370, no. 1674 (2015): 20140254. https://doi.org/10.1098/rstb.2014.0254. ↵
- Saini, M., & Kumar Kapoor, A. (2016). Biometrics in forensic identification: Applications and challenges. Journal of Forensic Medicine, 1(2). https://doi.org/10.4172/2472-1026.1000108 ↵
- Saini, M., & Kumar Kapoor, A. (2016). Biometrics in forensic identification: Applications and challenges. Journal of Forensic Medicine, 1(2). https://doi.org/10.4172/2472-1026.1000108 ↵
Tags from the story
Nomination-Social-Sciences
Recent Comments
Muhammad Hammad Zafar
Very informative article, it should not be taken easy and lightly and the use of palmprints that is similar to fingerprints which is unique for everyone can be used for further easiness in forensic science and investigations.
27/04/2023
2:29 pm
Hunter Stiles
Congratulations for being nominated! First of all, thank you for writing on such a fantastic subject! It’s a tremendously essential subject, especially given how quickly technology is developing in today’s world. It is crucial to acknowledge both the amazing space that technology has produced and the ramifications that it has also brought about. Our privacy and safety are now at stake due to the technological technologies we use. Regarding the things we permit in our daily life, we should be extremely cautious. Overall, this is a fantastic subject to discuss, especially with the development of technology. Super informative and well structured. Very well done!
27/04/2023
2:29 pm
Maximillian Morise
A fascinating article on the increasing ethical dilemmas that new technologies continue to present to the modern day world, and how we as societies are not properly prepared for their continued innovation and perfection. This one in particular has left me a lot to think about in regards to privacy and personalization. Congratulations on your nomination!
30/04/2023
2:29 pm
Karicia Gallegos
Congrats on your nomination! Thank you for sharing your thoughts on the use of biometric identifiers and the ethical concerns surrounding the collection and storage of this data. It is true that electronic devices like phones and laptops often come with accessibility measures that use biometric data to restrict access to others. This data is typically collected through fingerprints, facial recognition, eye scanners, voiceprints, or other methods, and can also be accessed through other smart devices like smartwatches and fitness trackers. Your article was so informative! Overall, great job!
02/05/2023
2:29 pm
Christian Lopez
Mia I think this is a perfect topic considering the current events that are happening with social media platforms in the United States. Its crazy to see that there is little to no laws that are structured around this considering the modern age of technology that we are in now.
08/05/2023
2:29 pm
Natalia Bustamante
Hi Mia! Firstly, I would like to acknowledge such a great topic that you wrote about! It is really an important topic, especially with the rise and advancement of technology in this current society. It is so important to thank technology for the incredible space it has created, but also acknowledge the implications it has also created. Having such advanced technology has put our safety and privacy at a risk. We should be very careful regarding what we allow in our daily lives. Overall, such a great topic to talk about especially with the rise of technology.
24/04/2023
2:29 pm